Find alternatives to Auth0

Managing authentication and access can be simpler and more secure with the right tools. Open-source platforms provide flexible and cost-effective solutions for individuals, teams, and organizations. In this blog, we’ve compiled a list of popular open-source tools like Keycloak, Logto, Authentik. From managing identity and access across applications to securely storing and sharing passwords or implementing multi-factor authentication, these tools offer practical solutions for modern security challenges. Read on to discover how these tools can help you streamline identity management and enhance security for your projects and workflows.
Keycloak
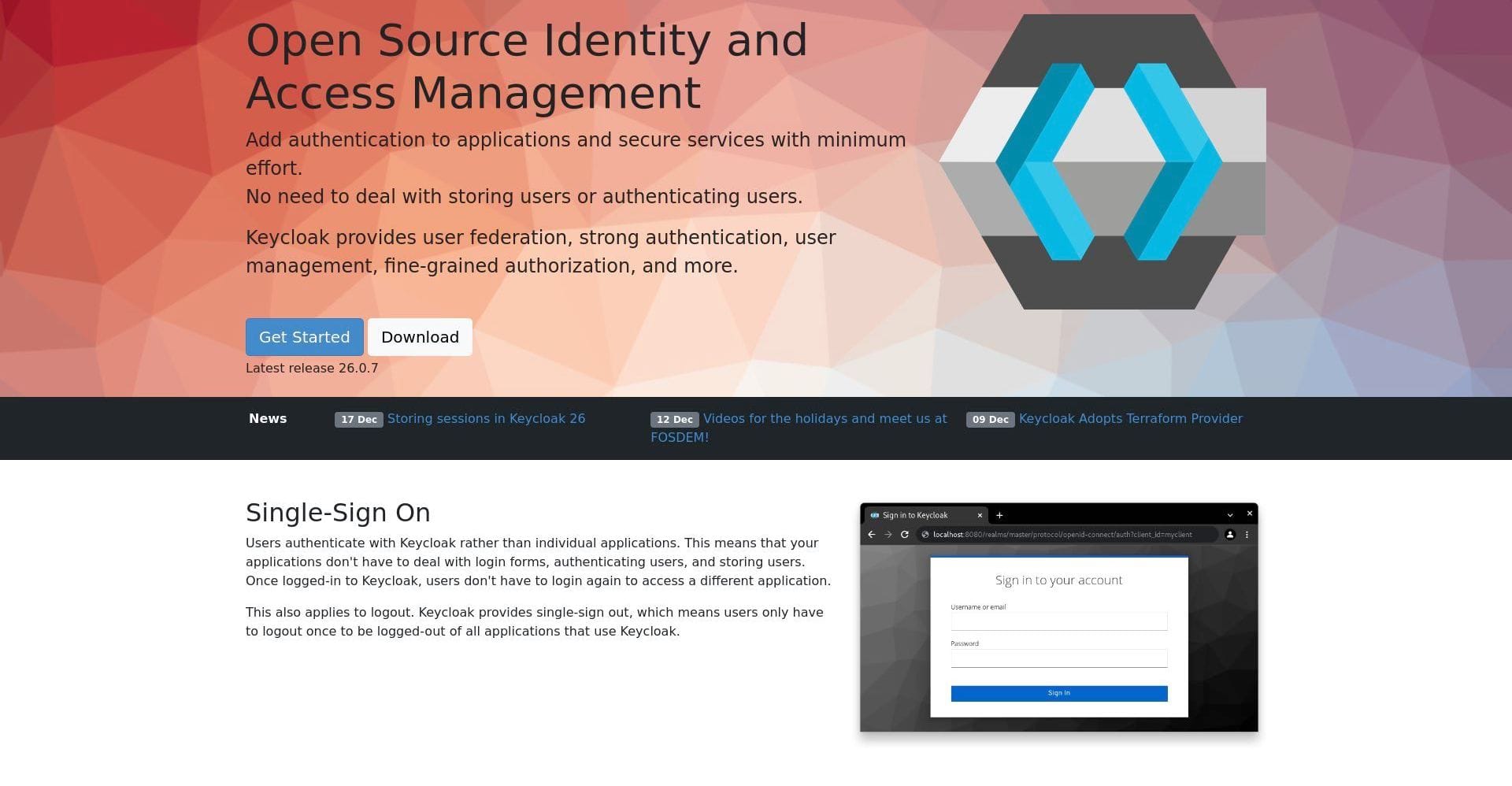
Secure your applications with seamless user authentication and access control.
An open-source platform for identity and access management, offering secure and flexible authentication for modern applications.
Keycloak is a powerful open-source identity and access management solution designed for modern applications and services. It simplifies the process of authentication and authorization, providing robust security for users and developers.
Keycloak is ideal for managing user identities, offering single sign-on (SSO), and integrating seamlessly with various platforms and protocols. With its customizable features, it’s a go-to choice for businesses seeking a secure and scalable identity solution.
Key features of Keycloak include:
- Single Sign-On (SSO): Allow users to log in once and gain access to multiple applications without re-entering credentials.
- Social Login: Integrate with social identity providers like Google, Facebook, and Twitter for easy user authentication.
- Fine-Grained Access Control: Use Keycloak’s built-in role-based access control (RBAC) to manage user permissions effectively.
- Customizable User Interfaces: Tailor login and registration pages to match your brand’s identity.
- Multi-Factor Authentication (MFA): Enhance security with MFA options, including SMS, email, or authenticator apps.
- Standards-Based Protocols: Support for industry-standard protocols like OpenID Connect, OAuth 2.0, and SAML ensures broad compatibility.
- LDAP and Active Directory Integration: Sync with existing directory services for streamlined user management.
- Extensibility: Customize Keycloak to suit your unique requirements using its robust extension model.
Keycloak is perfect for organizations of all sizes, whether you’re building new applications or integrating existing systems. Its open-source nature ensures transparency, flexibility, and cost-effectiveness.
Start using Keycloak today to secure your applications, streamline user management, and enhance your authentication workflows.
Logto
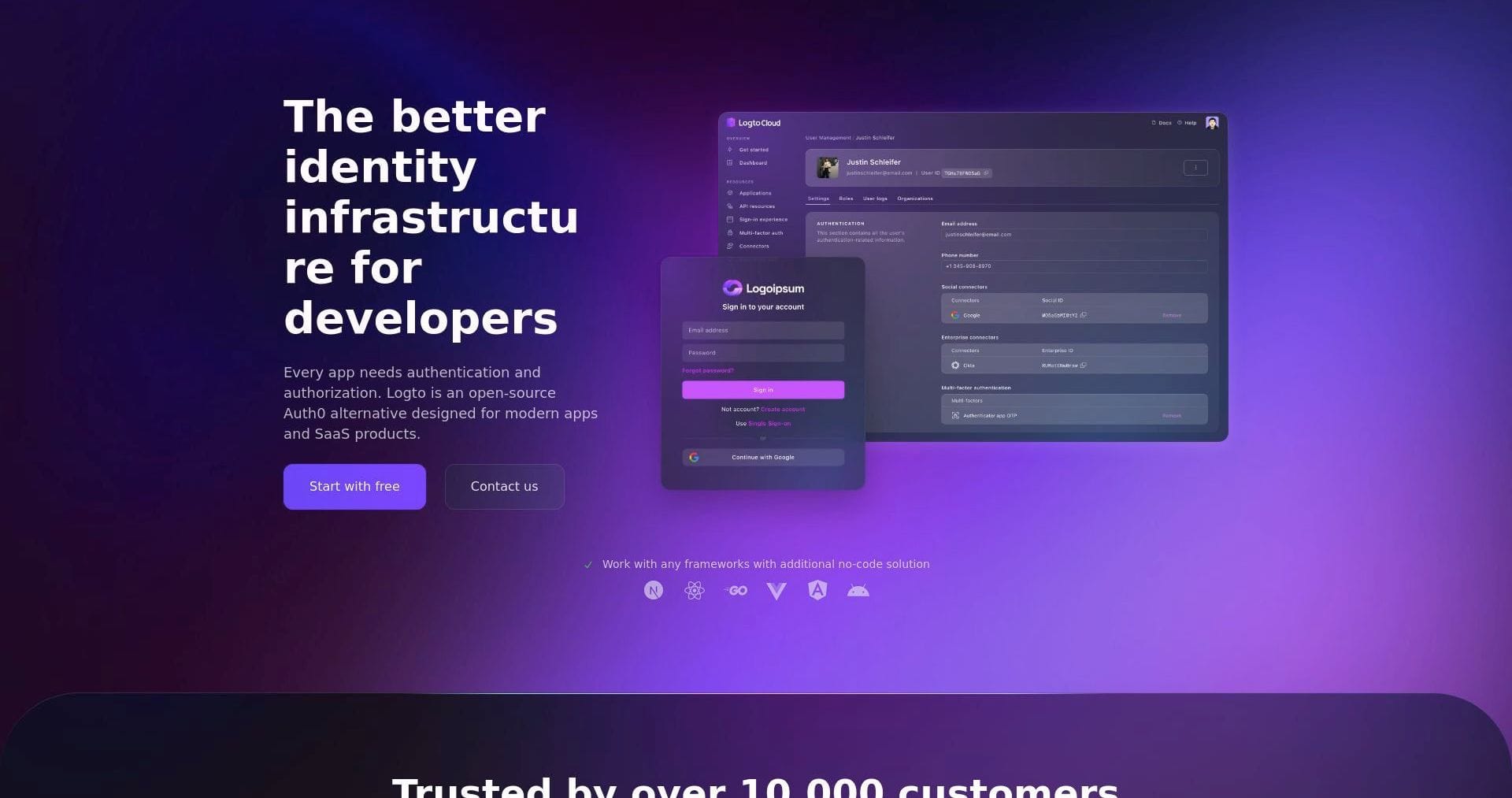
Streamline user authentication with a developer-friendly identity platform.
An open-source identity and access management solution designed for seamless integration with modern applications and APIs.
Logto is a developer-focused open-source identity and access management platform built for modern applications and APIs. It provides a simple yet powerful way to handle user authentication and authorization, making it easier for developers to focus on building features rather than managing identity infrastructure.
Logto is optimized for modern tech stacks, offering SDKs and APIs that integrate effortlessly with web, mobile, and server-side applications. With Logto, you can set up authentication flows, manage user permissions, and support social logins with minimal effort.
Key features of Logto include:
- Developer-Friendly APIs and SDKs: Comprehensive tools to integrate authentication seamlessly into your applications.
- Single Sign-On (SSO): Enable users to log in once and access multiple applications without re-authenticating.
- Social Login Support: Allow users to authenticate with popular platforms like Google, GitHub, and more.
- Role-Based Access Control (RBAC): Manage user permissions with fine-grained control.
- Customizable Authentication Flows: Tailor the login and registration processes to meet your application’s needs.
- Multi-Platform Support: Works seamlessly with web, mobile, and server-side environments.
- Built-In Audit Logging: Track authentication events to ensure compliance and enhance security.
- Secure Protocols: Support for OpenID Connect and OAuth 2.0 ensures compatibility and robust security.
- Open-Source Transparency: Benefit from an active community and complete control over your identity management.
Logto is designed to reduce the complexity of identity and access management, enabling developers to integrate robust authentication and authorization into their applications quickly. Its open-source nature and extensible architecture make it an ideal choice for startups, enterprises, and independent developers.

Authentik
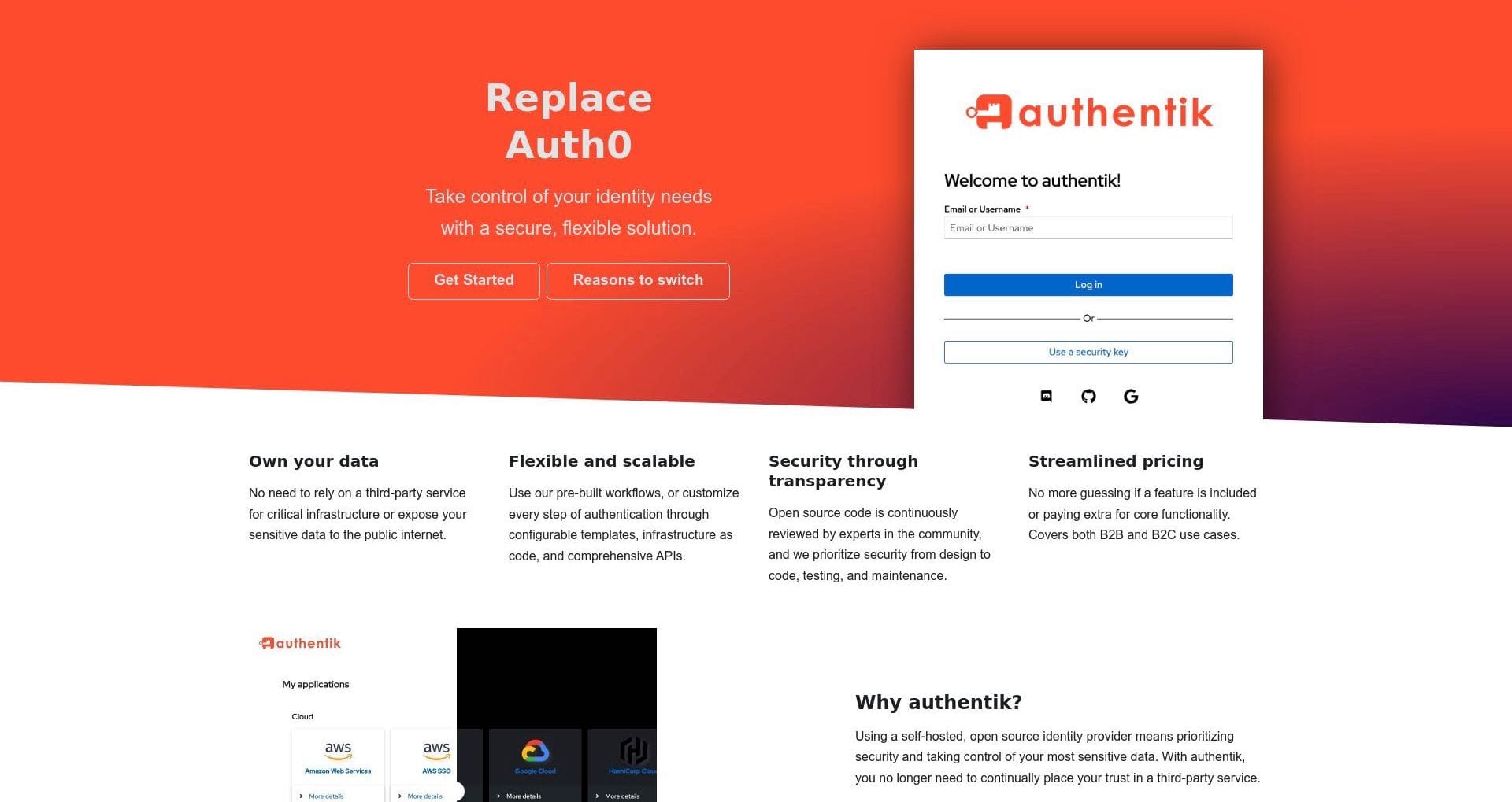
Simplify authentication and authorization with a customizable open-source identity platform.
An open-source identity provider offering secure, scalable, and highly customizable authentication solutions for modern applications and systems.
Authentik is an open-source identity provider designed to simplify authentication and authorization for modern applications. Built with flexibility and scalability in mind, Authentik provides robust features for managing user access while integrating seamlessly with existing infrastructure.
Its modular architecture and open-source nature make it a popular choice for businesses seeking a secure, customizable identity management solution. Authentik supports multiple authentication protocols, ensuring compatibility with various applications and services.
Key features of Authentik include:
- Single Sign-On (SSO): Simplify user login by enabling access to multiple applications with a single set of credentials.
- Protocol Support: Fully compatible with OpenID Connect, OAuth 2.0, SAML, and LDAP, ensuring integration with diverse systems.
- Multi-Factor Authentication (MFA): Enhance security by requiring an additional layer of authentication.
- Identity Federation: Connect with external identity providers to streamline user management.
- Customizable Workflows: Configure authentication flows to suit your organization’s needs.
- Group and Role Management: Assign permissions based on user roles and groups for better access control.
- Audit Logging and Monitoring: Track authentication events and ensure compliance with built-in logging capabilities.
- Extensible Design: Use Authentik’s modular architecture to create custom plugins and extend its functionality.
Whether you’re managing user access for internal tools, customer-facing applications, or third-party integrations, Authentik delivers the security and flexibility you need to handle identity management with ease.

Thanks for reading ❤️
Thank you so much for taking the time to read this article! We hope it helped you discover some valuable open-source tools that can simplify your authentication and security needs. Be sure to explore the official documentation for each tool to learn more about their features and capabilities. If you’re ready to try them out, take the next step and see how they can enhance your workflows and security practices. See you in the next one 👋
