Setting up Sign in with GitLab using Keycloak

Hey everyone, in this blog we will be setting up the "Sign in with GitLab" option using Keycloak. We will be using a self-hosted Keycloak instance deployed on Elestio. So, to get started head over to Elestio Dashboard and deploy and login into the Keycloak instance to get started. To set up GitLab as an identity provider in Keycloak, follow these detailed steps. Keycloak’s integration with GitLab allows users to log in using their GitLab credentials, simplifying authentication and enhancing security.
Creating a New Realm
According to the Keycloak documentation
A realm manages a set of users, credentials, roles, and groups. A user belongs to and logs into a realm. Realms are isolated from one another and can only manage and authenticate the users that they control.
Once you are logged in, head over to the drop-down menu on the top left. Notice that there is a default realm, Keycloak master which has higher privileges. To ensure a safer configuration, it’s recommended to create a new realm. Click on Create realm and add realm details, like the realm name. For example, here we’ll name it GitLab-Auth. After entering the details, click on Create to establish your new realm.
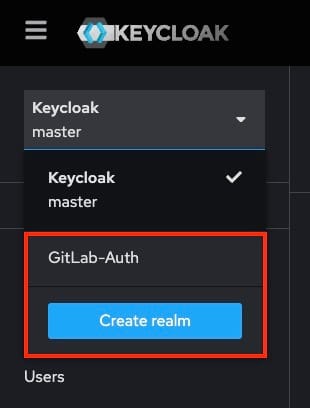
Initial Setup in Keycloak
With your new realm ready, navigate to the Identity Providers section. In the Social section, select GitLab to create a new GitLab identity provider integration. This action opens a configuration page where you’ll input the credentials needed to connect with GitLab.
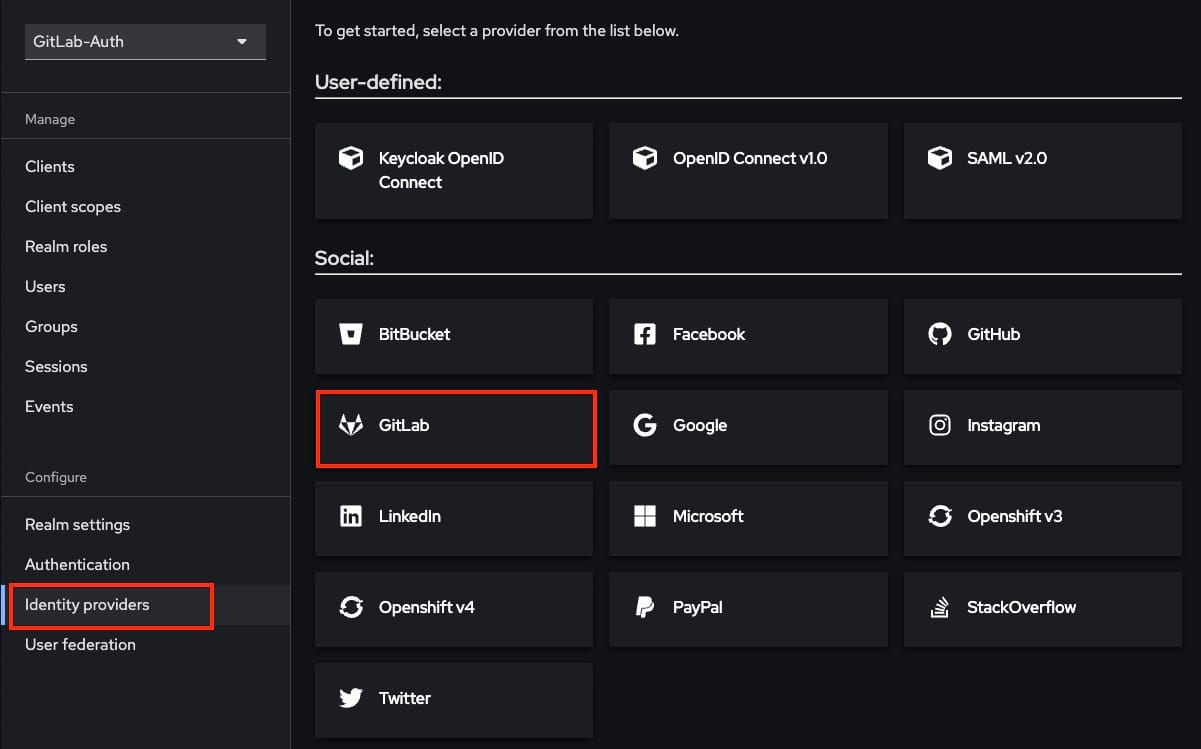
On this page, you’ll find a Redirect URI specific to Keycloak. Copy this URI, as you’ll need to register it in GitLab’s application settings in the next step. The Redirect URI is crucial, as it ensures a seamless login flow by redirecting users back to Keycloak after authenticating through GitLab.
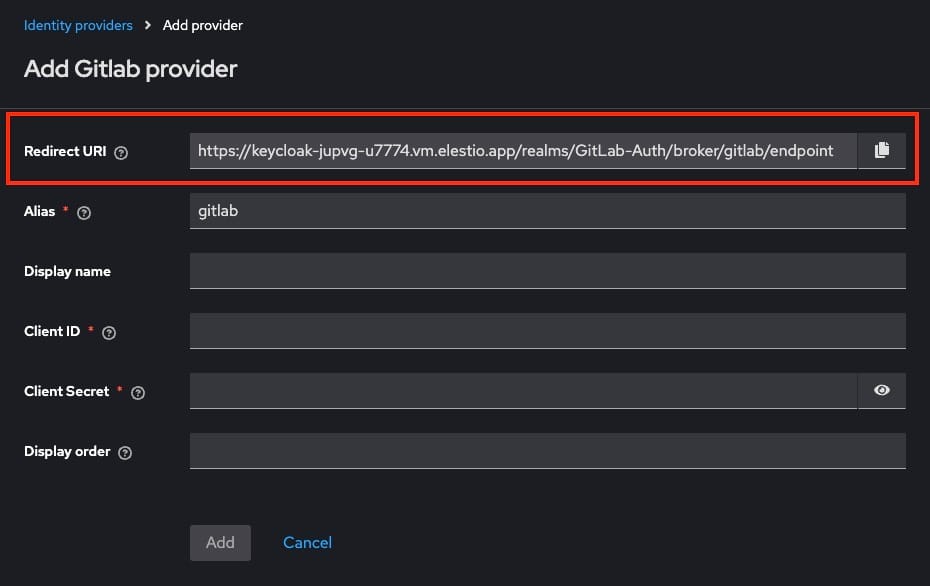
Register a New OAuth Application on GitLab
To enable GitLab login, you’ll need to register Keycloak as an OAuth application within your GitLab account. Start by logging into GitLab and going to Settings > Applications in your GitLab account. Click New Application to start the registration.
In the registration form, enter the required details:
- Name: A descriptive name for your app, such as "Keycloak Authentication".
- Redirect URI: Paste the Redirect URI you copied from Keycloak's GitLab identity provider setup page.
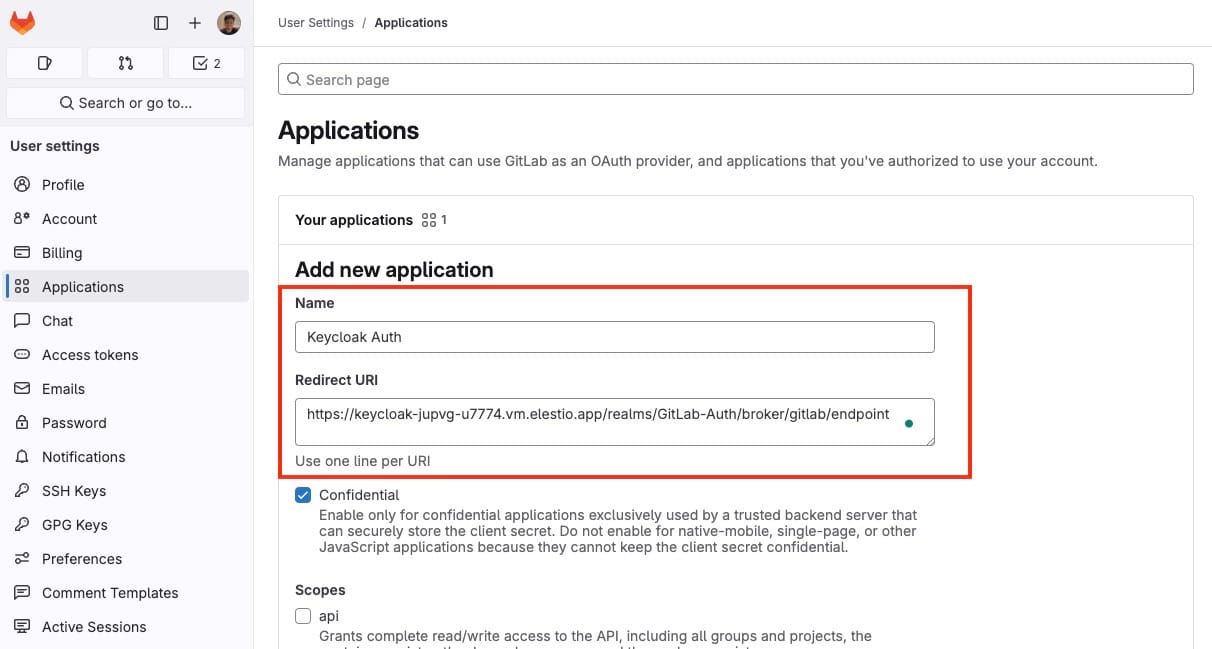
- Scopes: Select
openid,profile, and any other scopes required for your application.
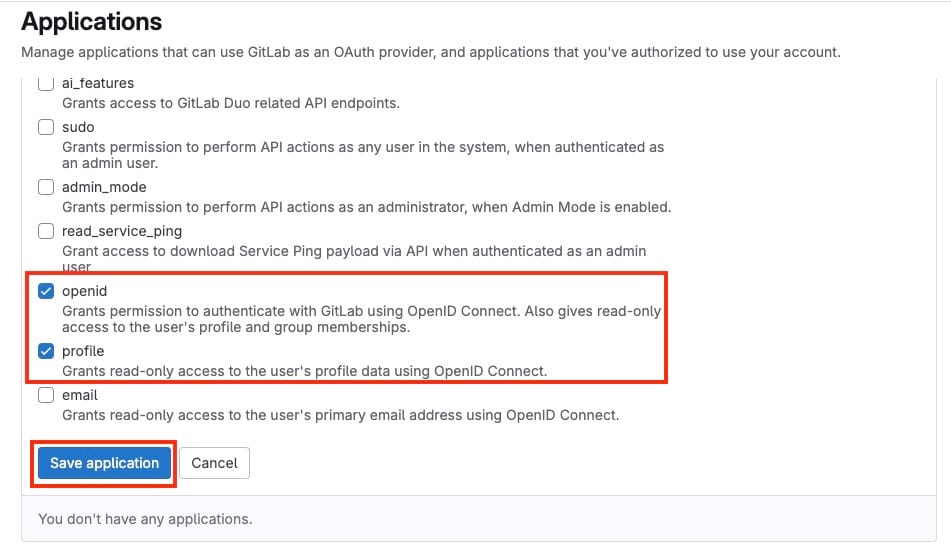
After filling out the form, click on Save application to register it.
Obtain Client ID and Client Secret
Once the application is registered, GitLab will provide a Client ID and Client Secret. These credentials are essential for Keycloak to communicate securely with GitLab for user authentication. Copy both the Client ID and Client Secret; you’ll need them for the next step.
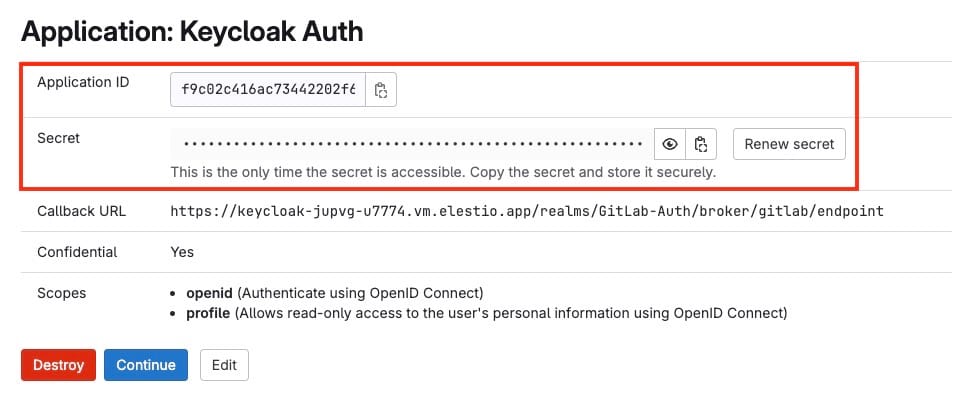
Enter GitLab Credentials in Keycloak
Go back to Keycloak’s GitLab identity provider configuration page and paste the Client ID and Client Secret into the respective fields. Save the configuration. Once saved, Keycloak will recognize GitLab as a valid identity provider, allowing users to authenticate using their GitLab accounts.
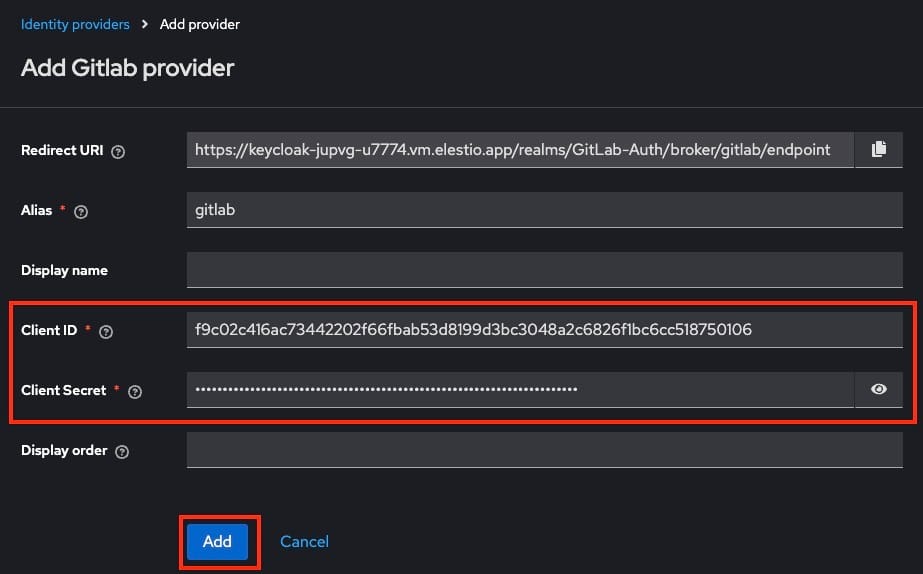
Additional Configuration
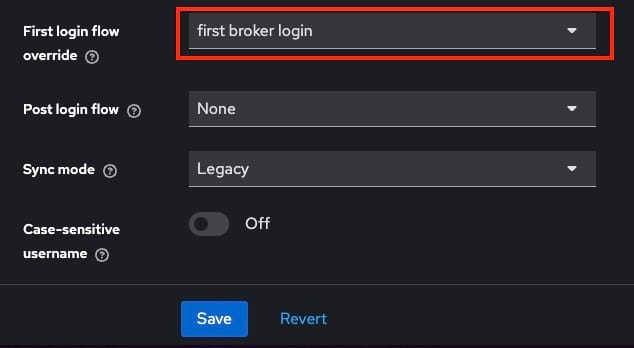
To ensure a smooth first-time login experience, scroll down in the GitLab provider settings until you find the First Login Flow option. If it’s not set to First Broker Login by default, change it to this option. This ensures that users logging in for the first time with GitLab will go through the appropriate login and account linking flow.
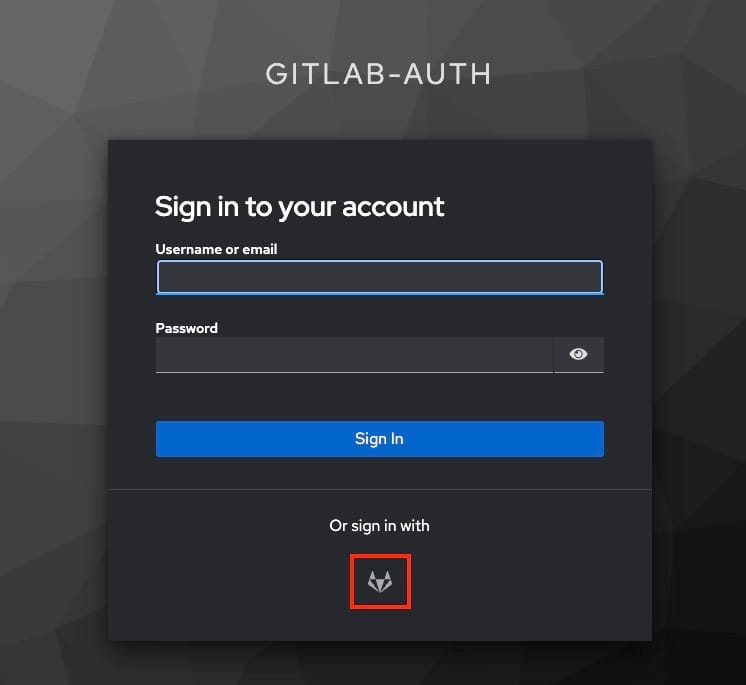
With everything configured, navigate to the login URL specific to your new realm. You should now see an option to Sign in with GitLab. Test the integration by logging in with your GitLab credentials to confirm that everything is working correctly.
Thanks for reading ❤️
Thank you so much for reading and do check out the resources provided to learn more about the Keycloak. You can click the button below to create your service on Elestio and implement this authentication method. See you in the next one👋